# MIRACL Trust Application Setup
An application on the MIRACL Trust platform is required. It is used by the Trusted IdP created in the OneLogin platform. Learn how to register a new app here.
# Node for Authentication Trees
# Integration Manual
The steps of reference integration constructing are listed below.
- Deploy Access Manager (AM) 6 as described in the ForgeRock manual.
- Go to AM realm dashboard. Open “Authentication - Trees”.
- Click “(+) Create Tree”.
- Fill the form.
- Tree Name:
"MIRACL"
- Tree Name:
- Click “Create”.
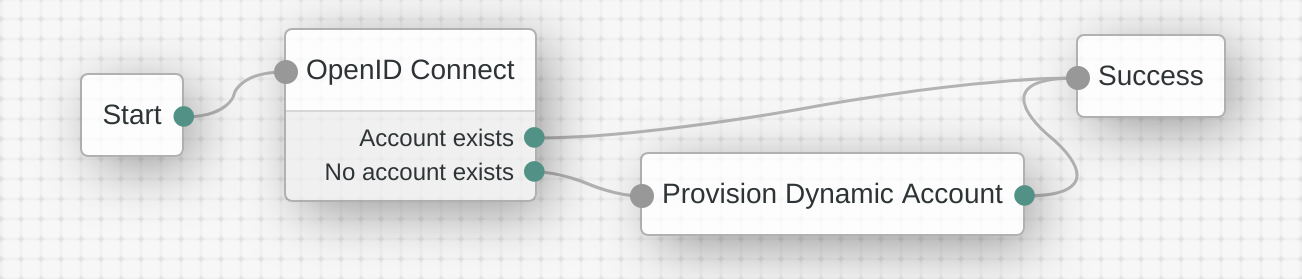
The GUI tree builder appears. Initially it contains two connected nodes -
"Start" and "Failure".
- In the “Components” section at the left, find “OpenID Connect” one and drag it
to the working area. Do the same for “Provision Dynamic Account” and “Success”
components. You should have the following components at the working area:
- “Start”
- “OpenID Connect”
- “Provision Dynamic Account”
- “Success”
- Click the “OpenID Connect” component. Properties list appears at the right.
- Fill the form.
- Node Name:
"MIRACL" - Client Id:
The OIDC application Client ID from MIRACL Trust Portal - Client Secret:
The OIDC application Client Secret from MIRACL Trust Portal - Authentication Endpoint URL:
"https://api.mpin.io/authorize" - Access Token Endpoint URL:
"https://api.mpin.io/oidc/token" - User Profile Service URL:
"https://api.mpin.io/oidc/userinfo" - OAuth Scope:
"openid" - Redirect URL:
The URL where AM is deployed - Social Provider:
"MIRACL" - Auth ID Key:
"id" - Use Basic Auth:
Off - Account Provider:
"org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvider" - Account Mapper:
"org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper" - Attribute Mapper:
"org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper" - Add the following entry to Account Mapper Configuration. You have to click
“Add” button first for subform to popup and click “+” button after finished:
"sub":"uid"
- Add the following entries to Attribute Mapper Configuration. You have to
click “Add” button first for subform to popup and click “+” button after
finished:
"sub":"uid""email":"mail"
- Save Attributes in the Session:
Off - OpenID Connect Mix-Up Mitigation Enabled:
Off - Token Issuer:
https://api.mpin.io - OpenID Connect Validation Type:
JWK URL - OpenID Connect Validation Value:
https://api.mpin.io/oidc/certs
- Node Name:
- Now nodes should be connected in the given way. Node input is located at the
left, and output(s) at the right. Connection is performed by dragging some
output to a required input.
- Connect “Start” node output to “MIRACL” node input.
- Connect “MIRACL” node output saying “No account exists” to “Provision Dynamic Account” node input.
- Connect “Provision Dynamic Account” node output to “Success” node input.
- Click “Save”.
# Test the Integration
- Go to AM realm dashboard. Open Authentication - Settings.
- Go to “Core” tab.
- Select Organization Authentication Configuration:
"MIRACL"
- Select Organization Authentication Configuration:
- Click Save Changes.
- Once you change that, the default log in to AM is
"MIRACL"tree. If you want to go back to the administrator window to make changes to the configuration, go to AM URL by appending"/console"(for example,"http://openam.partner.com:8080/openam/console"). This uses the administrator service to log in to AM (which should be the"ldapService"). - Log out of Access Manager and try to log in again.
- AM should automatically redirect you to the MIRACL Trust identity provider.
# Authentication Module
# Integration Manual
The steps of reference integration constructing are listed below.
- Deploy Access Manager 5.5 as described in the ForgeRock manual.
- Go to AM realm dashboard. Open Authentication - Modules.
- Click (+) Add Module.
- Fill in the form.
- Name:
"MIRACL" - Type:
"Social Auth OpenID"
- Name:
- Click Create.
- Fill in the form.
- Social Provider:
"MIRACL" - Client ID:
The OIDC application Client ID from MIRACL Trust Portal - Client Secret:
The OIDC application Client Secret from MIRACL Trust Portal - Authentication Endpoint URL:
"https://api.mpin.io/authorize" - Access Token Endpoint URL:
"https://api.mpin.io/oidc/token" - User Profile Service URL:
"https://api.mpin.io/oidc/userinfo" - Use Basic Auth:
Off - Subject Property:
"uid" - Proxy URL: Leave the default value which should be something like this
"http://xxx.xxx/openam/oauth2c/OAuthProxy.jsp"wherexxx.xxxis your domain- Go to the MIRACL Trust Portal.
- Set Redirect URL to:
Proxy URL.
- Token Issuer:
"https://api.mpin.io"
- Social Provider:
- Click Save Changes.
- Go to OpenID Connect tab.
- OpenID Connect validation configuration type:
jwk_url - OpenID Connect validation configuration value:
"https://api.mpin.io/oidc/certs"
- OpenID Connect validation configuration type:
- Click Save Changes.
- Go to the Account Provisioning tab.
- Fill in the form.
- Account Provider:
"org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvider" - Account Mapper:
"org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|MIRACL-" - Account Mapper Configuration:
"id=iplanet-am-user-alias-list" - Attribute Mapper:
"org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|iplanet-am-user-alias-list|MIRACL-" - Attribute Mapper Configuration:
"personal.last_name=sn id=uid email.email=mail personal.nickname=cn personal.first_name=givenName"
- Account Provider:
- Click Save Changes.
- Go to Authentication - Chains.
- Click (+) Add Chain.
- Fill in the form.
- Name:
"MIRACLAuthenticationService"
- Name:
- Click Create.
- Click (+) Add a Module.
- Fill in the form.
- Select Module:
"MIRACL" - Select Criteria:
"Required"
- Select Module:
- Click OK.
- Click Save Changes.
- Go to Authentication - Settings.
- Go to User Profile tab.
- Select User Profile:
"Ignored"
- Select User Profile:
- Click Save Changes.
- Go to Services.
- Click Social Authentication Implementations.
- If there is no such entry, click (+) Add a service, and choose a service type “Social Authentication Implementations”.
- Fill in the form “Display Names”.
- Key:
"MIRACL" - Value:
"MIRACL"
- Key:
- Click (+) add.
- Fill in the form “Authentication Chains”.
- Key:
"MIRACL" - Value:
"MIRACLAuthenticationService"
- Key:
- Click (+) add.
- Fill in the form “Enabled Implementations”.
- Add
"MIRACL"
- Add
- Click Save Changes.
# Test the Integration
- Go to the AM realm dashboard. Open Authentication - Settings.
- Go to Core tab.
- Select Organization Authentication Configuration:
"MIRACLAuthenticationService"
- Select Organization Authentication Configuration:
- Click Save Changes.
- Once you change that, the default log in to AM is the
"MIRACLAuthenticationService"tree. If you want to go back to the administrator window to make changes to the configuration, go to AM URL by appending"/console"(for example,"http://openam.partner.com:8080/openam/console"). This uses the administrator service to log in to AM (which should be the"ldapService"). - Log out from Access Manager and try to log in again.
- AM should automatically redirect you to the MIRACL Trust identity provider.