# Setting up MIRACL Trust SSO as an Identity Provider Within Expensify
These instructions are up-to-date at the time of writing, but you should refer back to the Expensify page on SAML IdP access to check for any changes. We cannot guarantee the accuracy of our SP-specific guidance.
-
Log in to Expensify (as administrator).
-
To enable SSO in Expensify you first need to have Domain Control enabled.
-
Once you have Domain Control enabled, navigate to Admin > Domain Control > [domain name] > SAML to display the following page.
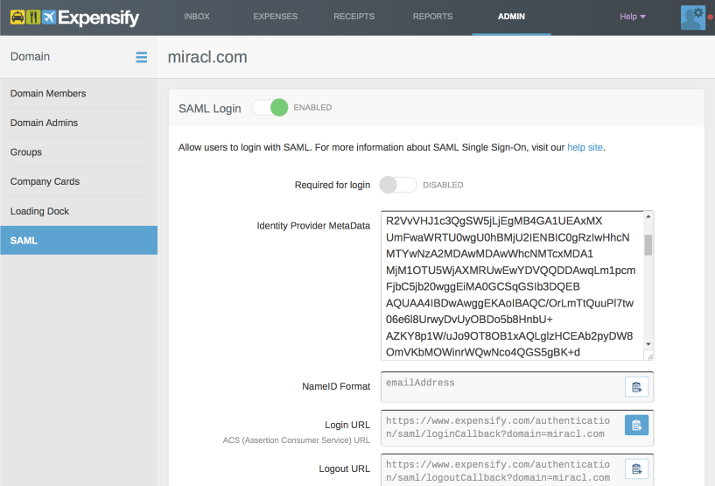
-
Find the MIRACL Trust metadata document – you should have downloaded this as an XML file (available at the following endpoint:
http://<yourssoip>/metadata). Note that, for a production setup, if you manually download your IdP metadata file, the validUntil date at the top of the file needs to be edited to an appropriate date (it defaults to 48hrs from the current date). -
Copy and paste the MIRACL Trust metadata into the Identity Provider MetaData text box.
-
Make a note of the endpoint in the Login URL field.
-
Make a note of the endpoint in the Logout URL field.
-
Scroll down to display the second half of the page:
-
Copy the contents of the Service Provider MetaData field into a text file.
-
Authorise SAML in Expensify by clicking on the ‘SAML Login’ ENABLED switch.
# Configuring Your Expensify Service Provider Profile With MIRACL Trust SSO
-
Edit
/etc/miracl-sso/service_providers/expensify.yaml:sp: expensify: description: expensify name: Expensify relay_state: "" login_url: https://www.expensify.com/authentication/saml/loginCallback?domain=example.com logout_url: https://www.expensify.com/authentication/saml/logoutCallback?domain=example.com metadata: >- <!-- insert downloaded SP metatadata here --> sign_response: true sign_assertion: true encrypt_assertion: false authorize: - - email: ^[^@]+@example.com$ -
Note that the name under which the SP is registered in the sp section is used to create your IdP-initiated login url, i.e.
https://<yourssoip>/login/expensify. -
Update the SP login_url and logout_url entries with the correct information retrieved from Expensify.
-
Expensify should supply you with your SP metadata which can be pasted into the above metadata field.
Note that, if you are using JSON format for your config file, the downloaded metadata should be saved as an xml file and converted to a single line with the " characters escaped with \ to meet json structure requirements. This can be achieved by running the following command on the downloaded metadata.xml file:
echo -e "\n"$(cat metadata.xml | tr -d '\n' | sed -E 's/"/\\"/g')"\n"The contents then are output in the terminal in a format that can be pasted into the metadata field of a JSON file.
-
In the authorize subsection, you can control what users are allowed to attempt login by following one or both of the below steps:
- Call up an LDAP setup from an
ldap.yamlfile stored in/etc/miracl-sso/integrations. - Configure a regex list of email addresses/domains. The above config shows
an example of how you would use
email: ^[^@]+@example.com$to only allow users from a certain email domain to login.
Note that if this is not set correctly, you receive ‘unauthorized user’ messages.
For more detailed info on using LDAP, API and/or regex to control authorized users, please see the authorization menu section.
- Call up an LDAP setup from an
-
Save and close the file.
-
In your /etc/miracl-sso/config.yaml file make sure you add
expensify.yamlto the list of ‘includes’:includes: - core.yaml # service providers - service_providers/expensify.yaml -
As always after config changes, restart the server.
-
Now your service is configured, you can visit
https://<yourssoip>/login/expensifyorhttps://<yourssoip>/servicesto login to the service using IdP-initiated login, or visit the Expensify login page and SP-initiated login are triggered automatically. -
You are able to login using the in-browser PIN pad or with the MIRACL Trust app. When logging in to your SSO service for the first time you are asked to register an email address so as to confirm your identity and register you as a user.