These instructions assume you have a running installation of the FortiGate firewall service. Screenshots in this documentation are from Fortigate VM64 v.6.0.6 but the instructions should be applicable for every version. We also assume that you have already registered in the MIRACL Portal and have created a MIRACL Trust app to obtain API keys as detailed in the Installation section.
# MIRACL Trust RADIUS Setup
For new settings to take effect, the service needs to be restarted.
Make sure your /etc/miracl-radius/config.yaml lists the correct files to
include (you need to add a hosts/fortigate.yaml file to it):
includes:
- core.yaml
- hosts/fortigate.yaml
Open your /etc/miracl-radius/core.yaml file and edit the mfa section to
include the client id and client secret from your app (as created in the MIRACL
Trust administration portal in the Installation section):
server:
address: :1812
otp_address: :8000
protocols:
- pap
- chap
- mschapv1
mfa:
global:
client_id: <YOUR_CLIENT_ID>
client_secret: <YOUR_CLIENT_SECRET>
If you need to enable accounting functionality, you need to add
./integrations/accounting.yaml to the includes of the
/etc/miracl-radius/config.yaml too:
includes:
- core.yaml
- hosts/fortigate.yaml
- integrations/accounting.yaml
and change it if necessary. Here are the default values:
/etc/miracl-radius/integrations/accounting.yaml
server:
accounting:
address: :1813
storage:
file:
path: ./acct.log
Then edit your /etc/miracl-radius/hosts/fortigate.yaml file. Add the IP of
your FortiGate server and the shared secret (a strong and hard to guess
arbitrary string) that should also be entered in the FortiGate admin console
too. For the purposes of this simple demo you can also use the mfa_id
parameter to allow for a non-email username. The example below means that you
can use the first half of an ‘@mycompany.com’ email address as your username for
logging into FortiGate (e.g. ‘john’ from ‘john@mycompany.com’):
host:
172.17.0.1:
name: fortigate
authorize: true
mfa: global
mfa_id: '{{.UserID}}@mycompany.com'
secret: 'fortigateSecret'
# return_attributes:
# Acct-Interim-Interval: 600
# Vendor-Specific:
# Fortinet:
# Fortinet-Group-Name: MyGroup
Using authorize: true on its own would mean that anybody would be permitted to attempt to login, but combining it with mfa_id: ‘{{.UserID}}@mycompany.com’ means that only users with the @mycompany email domain are authorized. The LDAP and authorization section explains how LDAP or simple regex of email domains can be used for more detailed control of lists of users authorized to attempt to login.
If you need your radius server to return any properties to the radius client
(the FortiGate service in this case), you could use the
return_attributes functionality and
specify the ones you desire.
Do not confuse Client Secret with Secret! Client Secret is the OIDC Client Secret of the MIRACL Trust API and Secret is the arbitrary secret that must be specified both in the MIRACL Trust RADIUS Server config.json and the FortiGate admin UI so they can authenticate to each other.
# Note on User Authentication
To generate OTP users need to register first. Registration is outlined in the OTP Generation page. Authentication to FortiGate could be done using a user identifier and not an email. This is achieved using the mfa_id configuration option of the MIRACL Trust RADIUS Server which transforms the email to user identifier.
# FortiGate Configuration
It is important port 1812 (UDP) (and 1813 (UDP) if accounting used) to be open as the radius packets are sent through it.
We suppose you have a proper VPN setup and can successfully connect via FortiClient to the FortiGate service without a radius setup.
In order to add a radius server for authentication to the FortiGate server, you
need to open the FortiGate admin panel and go to User & Device >
RADIUS Servers and click + Create New button. You need to fill the required
IP/Name of your running MIRACL Trust Radius server and the shared secret you
have already entered in the server radius config host file.
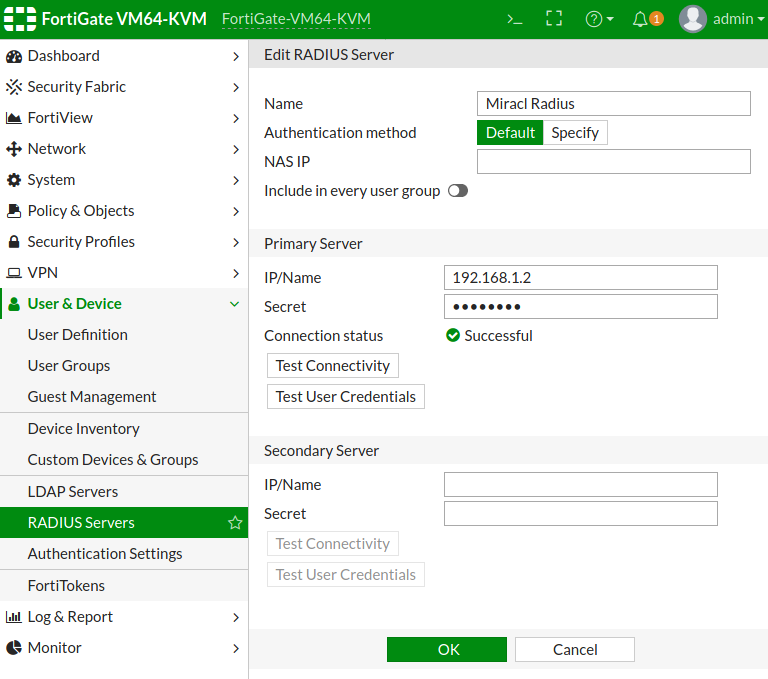
# Test With FortiGate Web Interface Tool
If you have properly setup your connection the Test Connectivity button should
return Successful. Have in mind that this button only check if it has any
response from the radius server and does not check if it is a success or a
reject packet. If you’d like to check the type of the response too, you need to
use the Test User Credentials button, to generate an OTP
for a registered email and enter your email and OTP in the requested fields. If
you have set the mfa_id in the RADIUS server host configuration, you can use
only the email name instead of the entire one (e.g. ‘john’ from
‘john@mycompany.com’) for a username.
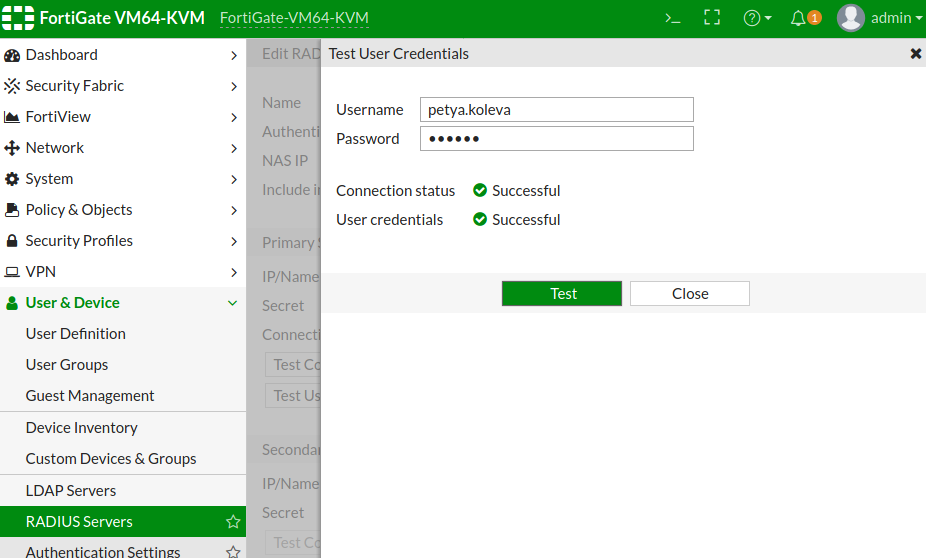
# Setup User Group
You need to create a user group to authenticate with the created RADIUS server.
Navigate to User & Device > User Groups and click + Create New button.
It’s important to choose Firewall for a type of the group. Enter an
appropriate name and add the created RADIUS server as a Remote Group.
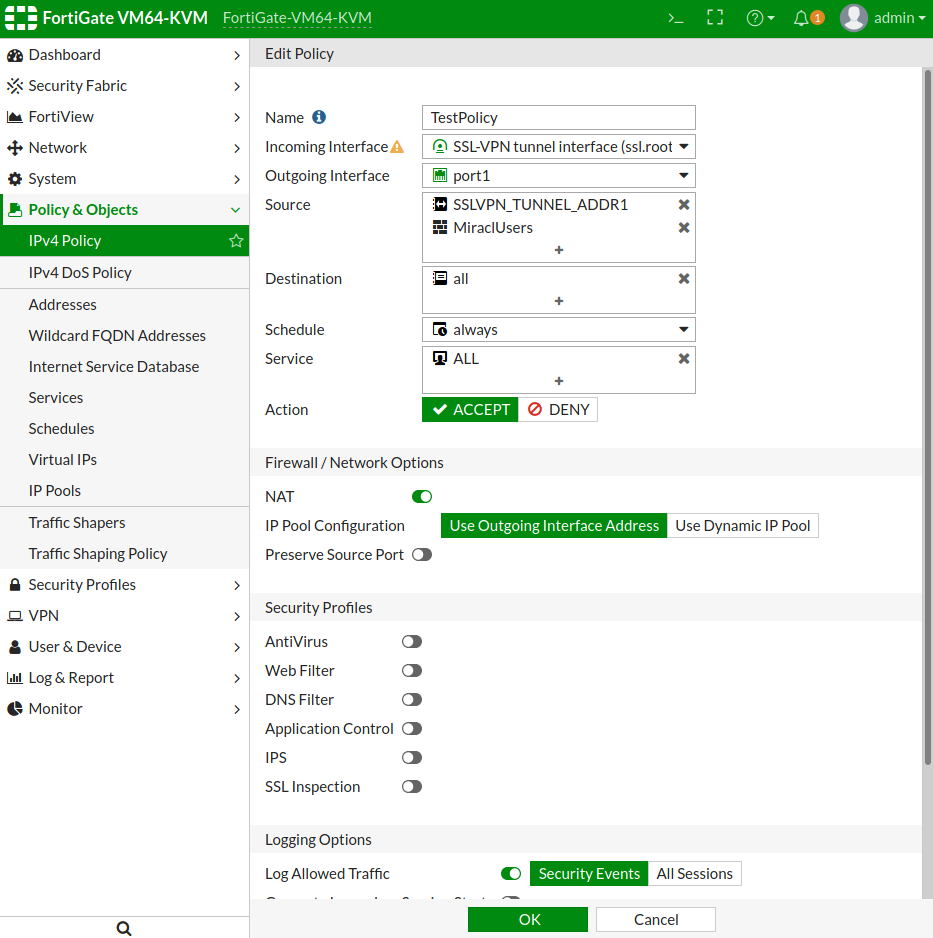
You need to have setup a proper IPv4 Policy setup for the SSL-VPN tunnel with
a Source the created RADIUS user group so you could authenticate with it using
a SSL VPN connection. Here is our test sample setup:
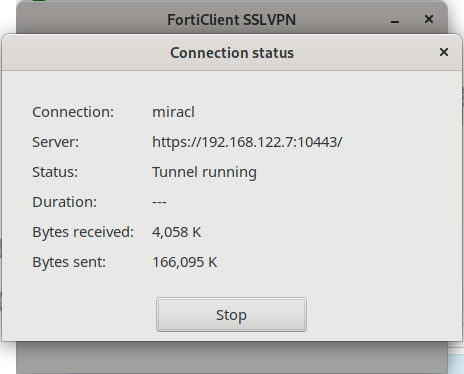
# Test With FortiClient
Your setup is ready and you could connect to your FortiGate service by the MIRACL Trust RADIUS server authentication using the FortiClient SSLVPN tool. You need fist to generate an OTP for a registered email. Then enter the FortiGate server IP and port in the requested FortiClient fields. Enter your username (if using mfa_id it should be only the first part of the mail you just generated an OTP for) and the generated OTP in the User and Passwords field.
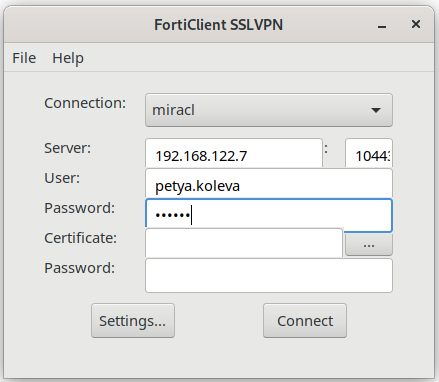
When you click the Connect button you should see a similar screen: