
One question we often come across is ‘what is Zero Trust’ and if it is related to a ‘Zero Knowledge Proof’? So, today, in his summer series of new, insightful blogs, the CCO at MIRACL, Michael Tanaka, explains all…
Like a lot of cyber security concepts, this one is relatively poorly understood yet actually quite simple in its goals.
Historically security has been designed around a strong perimeter and similar to a turtle, a hard exterior keeps out the obvious attackers but unfortunately for the turtle, not every attack fits the defence. In fact most successful attacks purposefully circumvent the defence. Being an animal lover, I’ll try to avoid a metaphorical slaughter of a turtle in the rest of this article but let’s be frank, turtles die of a lot more than old age.
Back in the 60’s, computer defences began and ended at the perimeter password and in some ways that made sense. Only trusted parties could gain access to mainframes and once you had access there was very little you could do, other than reprogram your own session. Today’s environment is nothing like the 60’s with both internal and external services on multi-tenanted and virtual platforms available from anywhere around the world, accessible to both humans and machines.
So the point is that the perimeter has been blurred into relative obscurity by the introduction of technology….and this process will only continue as technology marches on.
As a simple illustration of the issue, let’s assume you’re in the pub having a drink with some friends. You check your balance to see if you can get the next round in and with a resounding flourish smack your phone on the table and head off to the bar. At that point an opportunistic “friend” decides to swipe your phone and transfer all your remaining cash to their own account. You were logged in, you were in an open session and you were abused.
Now you’re at your office and you sign into your brand spanking new Single Sign On (SSO) platform which gives you access to every resource you use in the office. You then step away to grab a coffee and someone else sits at your desk and decides to make some alterations, next thing you know. Your company is $5mln out of pocket, you’re out of a job and your “friend” is nowhere to be found!
OK, those examples are far too obvious and too easy, but now let’s assume we’re working from home and some not-so-friendly hackers have managed to remotely transfer your session tokens from your computer to their own….they now have a copy of your trusted session running with all of your resources and services. Or even more insidious, by simply gaining access to your HR system they change their privileges to ultimately gain access to other systems such as your accounting tools.
So what’s the answer?
Zero Trust of course! And this is where some of the confusion starts. Zero Trust is a user security model that acknowledges the fact that even an authenticated user cannot be trusted and should be re-authenticated whenever they access privileged services or data. Furthermore resources and access privileges should be micro-segmented to avoid unnecessary access and control. For the record, let’s not confuse this with Zero Knowledge Proofs (ZKPs) which are tamper resistant authentication protocols which avoid the transmission of sensitive data and, as such, justify their own, separate discussion.
The obvious way to create a Zero Trust environment is to continuously validate a user by re-authenticating whenever they access any services or resources, but in practice this is a tough challenge.
Re-authenticating users usually involves high friction, high failure and/or high cost. Often it is relatively insecure as well, reliant on passwords, OTPs and SMS texts which are all easily diverted, shared or stolen. Passwords, OTPs and SMS texts are all easy targets for social engineering attacks.
Surely, I hear you say, the time spent authenticating isn’t an issue?
Just consider the fact that authenticating twice per day using secure Multi Factor Authentication will take your average user 60 seconds out of every work day. Believe it or not, those two authentications per day represent 1 man year of lost time for a 500 person enterprise!
Or looked at another way, the average salaried user in London cost their business 0.75p per second. So 60 seconds wasted authenticating represents a £0.45 cost to the business for every employee for every work day.
From a B2C perspective it’s been shown that every 1 second delay can result in a drop of up to 20% in user conversion (successfully completing their journey).
So every second counts.
Where, and why, does user failure come into it?
If every action needs to be authenticated then every action can be derailed by any failure with the authentication. Failure can generally be attributed to two sources: 1) system failure where one or more steps to that process breaks or 2) user failure where the user either fumbles a step or simply gets distracted and never completes the task.
In the banking industry SMS text still comprises nearly 60% of all “secure” authentications that take place. That is incredibly surprising when you consider how vulnerable they are to misuse and attack, but for now we’ll ignore the obvious security elephant (I told you I love animals) in the room.
Think of it this way, when you operate an SMS authentication process you have numerous points of failure ie:
- 11.4% of users fail to enter the correct password on websites
- 38% of users don’t have their phone present when asked to authenticate
- 3% fail a biometric and 2.3% fail a pin or password to login to the phone
- 11-20% of SMS OTP texts never arrive increasing to 50% if the phone number hasn’t been verified
- 10% of users fail to transfer a six-digit code correctly
That means from the point of typing in your password to entering the correct OTP you could have a failure rate of over 50%. Additionally that process takes 30 seconds or more in most cases and costs 4p (UK AWS cognito SMS pricing) not including the rest of the infrastructure.
So what happens when someone logs into a banking app to make 3 payments. Currently, to reduce friction, many services will ignore the issues and use one SMS OTP, whereas they should really be using 4 - one for the primary login and 1 for each payment.
So why don’t we use multiple SMS One Time Passcodes?
Running 4 authentications using SMS OTP would:
- Require at least 20 distinct steps from the user
- Take the user around 2 minutes to complete
- We would expect 7 out of 10 people to fail at least one of the 4 authentications
- Cost the service anywhere from 24 - 40p depending on SMS cost, failure rates, infrastructure costs etc
So clearly this would cause too much friction, cost too much and result in constant failures and as a result, increased support costs and angry customers. Half of your employees would be up in arms if you even suggested it, or your customers would be nowhere to be seen.
If OTPs aren’t the answer, what about Biometrics?
Quite a bit has been made of biometric authentication’s promise to create the Zero Trust environment we need. The problem is that the reality of biometric authentication has not caught up the hopes.
Whilst we certainly acknowledge that biometric authentication will play a part in the future of security, the reality is that biometrics generally suffer from one or more of the following issues: speed, accuracy, availability of hardware, stability of result, cost, enrolment requirements and/or vulnerability to impersonation.
Recently much has been made of passive multimodal biometrics powered by things such as typing cadence, device movement, linguistic profiling and many more metrics of user interactions and again we have no doubt that for certain edge cases these technologies will have value but in the real world they fall far short of the mark.
Take for instance the best and most commonly overlooked example, Google’s “No Captcha reCaptcha’’. To the user, this appears to be a simple click of one check box, yet many believe it actually uses everything that Google can capture and characterise about you whilst interacting with any of their products. As we know, a considerable amount of data and far more than just about any other organisation will have to hand.
Yet, as we have all experienced, it fails frequently, falling back to simple visual challenges which yet again frustrate most users. It seems very few of us can identify busses, crosswalks or traffic lights with any degree of accuracy!
Understanding how often Google’s Captcha reCaptcha fails to identify the simple fact you’re human - it becomes much easier to appreciate how difficult it is for any other organisation to prove the much harder task of verifying you are really “you”.
It all comes down to usability
To us it’s no surprise that passwords still make up over 95% of all authentications. They’re relatively simple for users, can be deployed on any device and are inexpensive if you exclude the hidden costs. They score highly on a usability scale.
Usability is one of the primary reasons legacy Multi Factor Authentication technologies and Biometrics have failed to replace passwords. Nonetheless we’re now asking those same technologies to secure our Zero Trust environments where usability is even more important.
We clearly need something today….
It has to be highly dependable, quick, easy to use and inexpensive!
MIRACL’s highly secure MFA has only one user step, a failure rate of 0.5%-3%, takes less than 3 seconds and costs less than 0.5p (on volume).
So for those same 4 authentications using MIRACL Trust ID in the Zero Trust environment it would:
- Require 4 distinct steps from the user
- Take the user 8-12 seconds
- Expect 1 out of 10 people to fail at least one of the 4 authentications
- Cost the service less than 2p
Higher security, lower friction, lower cost, lower failure rates….it’s not even a fair comparison!
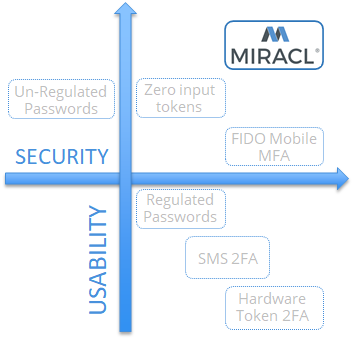
We help in the simplest way possible, by providing a secure authentication process that introduces the absolute minimum of user friction and user failure. Now your users can realistically authenticate as-needed rather than when-forced as would be the case using SMS OTPs.
….And it’s available today!
MICHAEL TANAKA, CCO of MIRACL - has over 30-years’ experience presenting complex technologies and concepts to a diverse range of technical and business audiences.
For further information & the latest updates please visit: MIRACL or follow us on social media: Twitter @MIRACL | LinkedIn MIRACL
To reach out to MIRACL about potential partnership opportunities email Kate Ellerton on kate.ellerton@miracl.com



