
In my previous blog last month, I highlighted how easily our credentials were sold on the dark web – and shared some alarming stats in relation to online consumer fraud and identity theft, particularly in relation to account takeovers. Today we assess the current rate of credential stuffing and question why this is continuing to increase at an alarming rate.
What is the current rate of credential stuffing?
In the last quarter we estimate there were over 10 billion credential stuffing attacks globally with high profile victims in the last few months including Spotify (350,000 accounts in November) and Activision (500,000 accounts in September). Perhaps a better measure is the ratio of attempted fraudulent logins over total logins which was estimated by Sift to have grown in Q3 2020 by 282% year over year. Growth rates clearly vary by both geography and sector but they appear to be highest in Europe with particular blackspots in entertainment-based sectors such as gaming, gambling, media and dating sites. Here, fraudulent bots may be responsible for the majority of the incoming traffic.
There has also been a specific pandemic-related spike in attacks on e-commerce operators of bulky goods where shop closures have caused a sudden shift to online delivery. Equally, hackers are focusing on the new trend of ‘BOPIS’ (buy online, pick-up in-store). In the historic targets of consumer-banking and payments sectors, password-based account takeover attacks are still high at approximately 30% of attacks but 70% of the fraud activity is centred around payments where reports suggest friendly fraud and chargebacks are fast growing problems.
This acceleration in password-related fraud rates has caught the attention of the SEC (Securities and Exchange Commission) via their division, the Office of Compliance Inspections and Examinations (“OCIE”), which on September 15th this year issued a Risk Alert.
Why is the rate of attacks growing?
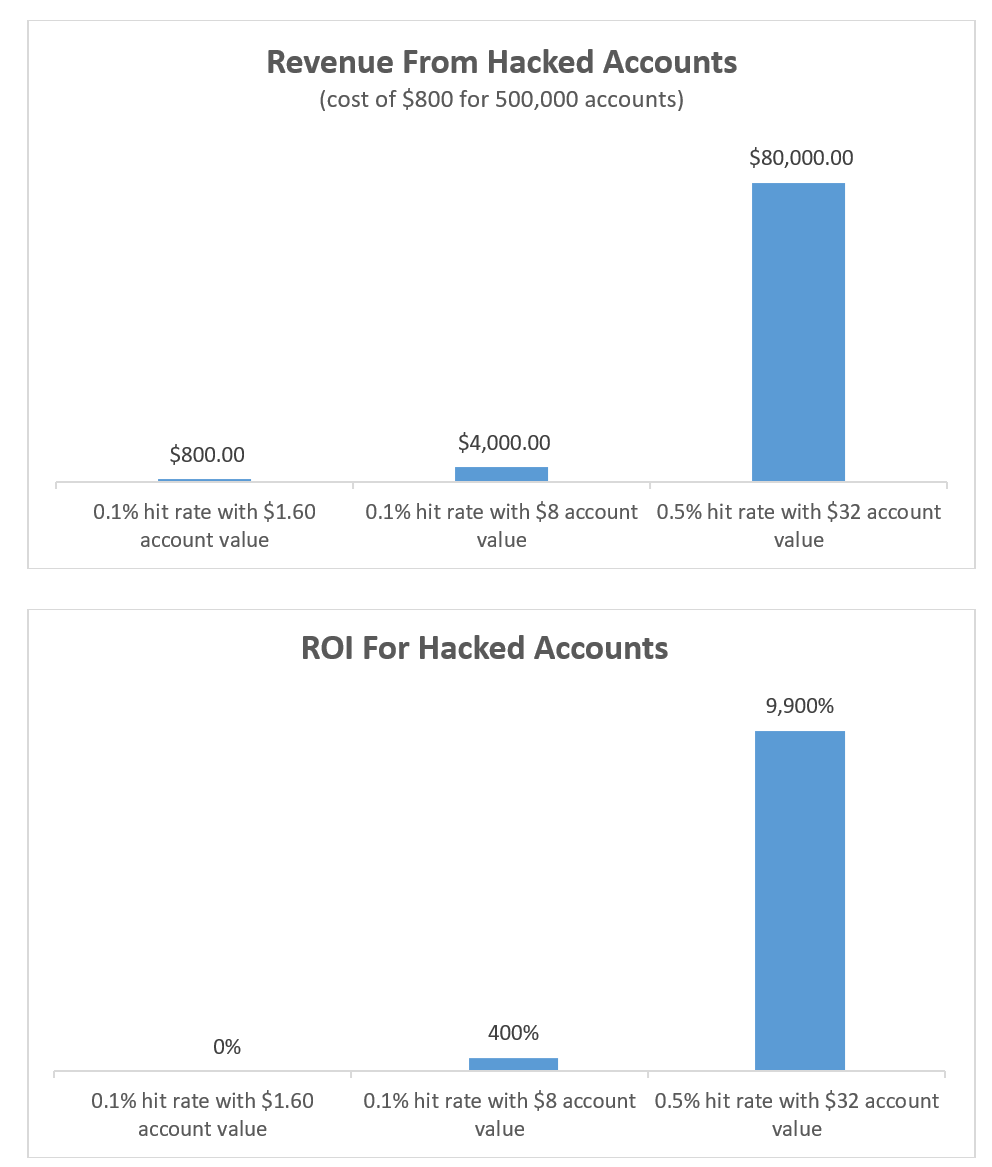
Put simply, the credential stuffing is incredibly profitable for hackers. For a turn-key basic credential stuffing rig using freely available ‘dumped’ passwords, there is a total ‘all-in’ cost of roughly $800 to hack 500,000 username and password combinations. This will include IP proxy rotation and a Sentry MBA stuffing application, which is highly configurable for specific use-cases.
The cost of making 500,000 targeted credential stuffing attempts equates to $0.0016 per credential. Success rates vary according to the quality of data but average between 0.1% and 1% (depending on the sector, age and geography). At the lowest hit-rates, a hacker would still be able to successfully compromise 500 accounts. Even if all of those hacked accounts only fetch the lowest market price per hacked account sold ($1.60), the hacker still basically covers his or her cost. However, the potential upside is huge. If the 500 (minimum) hacked accounts average $8 in value (conservative in our view), revenues are 5 times costs for a process that is speedy, fully scalable, requires little work and has a very rapid turnaround. If the hit-rate rises to 0.5% and the hacker nets $32 per hacked account, they will take away $80,000, which is 100 times their initial capital input. These are plausible numbers and go some way to explaining the scale that these nefarious activities have now taken on.
As long as these staggering profits continue, this problem is only going to grow, whether fuelled by poorly protected authentication databases, widely distributed credential-grabbing malware or aggrieved insiders selling confidential data on the side. Organisations need to implement authentication methods that protect against this form of attack. Most multi-factor authentication systems achieve this but typically they result in a poor user experience that negatively impacts sales conversion due to users having to wait for a separate code or visit a separate app. Not so with MIRACL. We prevent attacks such as credential stuffing and phishing but we also provide the only multi-factor authentication in the world that works with just one passwordless user input on any device ensuring that sales conversion is actually enhanced versus passwords.
Want to learn what the overall cost for this unwanted fraud is expected to be in 2020, both in direct compensation and incurred cost but also in lost customers? Follow my final blog later this month to find out…
Find out more about MIRACL’s highly secure online authentication that complies with PSD2 by visiting MIRACL or follow us on social media: Twitter @MIRACL | LinkedIn MIRACL



