One of the biggest issues in security today is that of secure identification and the misuse of stolen credentials to gain fraudulent access. This is highlighted in recent Verizon Data Breach reports: in the 2017 report it is revealed that 62% of data breaches featured hacking with 81% of these leveraging stolen or weak passwords; in the 2018 report the authors note the considerable number of breaches due to botnets using malware to capture login details and exclude them from their analysis since “due to the sheer number of them (over 43,000 successful accesses via stolen credentials), they would drown out everything else”.
In order to address this and move beyond the flawed username/password approach the industry is adopting two factor authentication where a one-time password or private key is used to further prove a user’s identity. Unfortunately this has come at the expense of usability with people being asked to carry secure dongles (such as with FIDO’s U2F) or smart-phone authenticators. The days of being able to login via a browser seem to be long gone.
As an aside, it is worth noting that the rush towards biometrics, whilst beguiling, is a big risk. NIST is not keen and for good reason, biometrics are more like a username than a password in that they can’t be changed. Would you be happy leaving your credit card PIN on every glass you touched? What happens if you want to change your biometric; once you’ve used all ten fingers you’re pretty much out of options…
So, why are we forced to accept this loss of usability? Quite simply it is because we need to keep secrets secure: for example, the best approaches tend to use public/private key pairs which require the private key to be stored securely in a secure dongle or secure storage in a phone; this also leads to the flawed chains of trust based on Certificate Authorities we see in PKI.
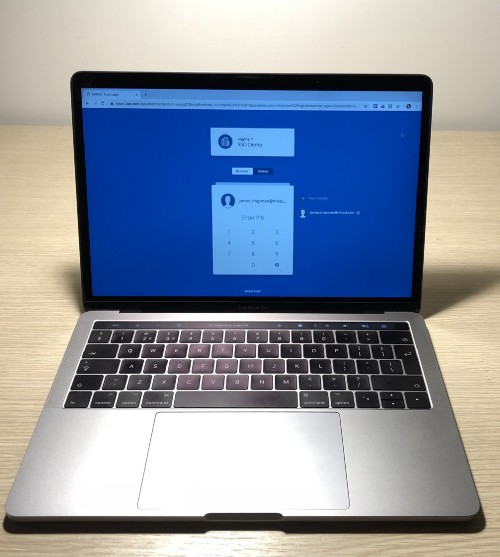
Secure 2-factor authentication in a browser: look no dongles!
We can address all these issues if only we could split our cryptographic secrets into pieces and store them separately. Luckily there is a technique, based on type-3 pairings on elliptic curves, that allows precisely this. This technique, whilst widely accepted in the academic community, is not used widely commercially where the vested interests of HW vendors and certificate authorities are strongly aligned with public/private key approaches.
MIRACL (www.miracl.com) has used this new technology to build a scalable Identity as a service offering in which all secrets, and hence trust, are distributed amongst multiple parties. For users in particular this means:
- No one has your secret except you and no single party has the means to recreate your secret
- Your secret can be split into a PIN and a token providing true 2-factor authentication without the need for secure storage.
- Your authentication now simply involves entering a PIN on your specific machine which is now as secure as a ‘Chip and PIN’ credit card
- Due to the true two-factor nature of the approach, your susceptibility to phishing is drastically reduced
By fundamentally changing our approach to authentication we can get back to a simple login via a web-browser but without incurring any loss in security. As proof of identity becomes increasingly important for citizens everywhere, this gives us reason to hope.



